Online Digital Forensics Courses and Labs
Building a Low-cost and State-of-the-art IoT Security Hands-on Laboratory
Funded by National Science Foundation (NSF)
Funded by Cyber Florida

Automatic Security Update Removal to Create Vulnerable Windows Virtual Machine
Instructor: Dr. Cliff Zou, 407-823-5015, czou@cs.ucf.edu
Goals of this tutorial:
- Learn how to set up vulnerable Windows OS virtual machine quickly using the provided script
- Help instructor or students to quickly set up penetration testing target and environment
Software Needed:
Set up Vulnerable Windows XP Virtual Machine:
Windows XP Mode Provided by Microsoft Windows 7 Virtual Machine Image
Microsoft originally provided Windows XP VM image download, but stopped providing it on its website after the company stopped service on WinXP. If you still need WinXP VM to conduct testing, you can obtain it via the WinXP mode in Windows 7 VM. We provided a lecture slides on how to do it under VirtualBox (ppt). Here is an example online tutorial webpage (link).
However, the WinXP VM derived through this way is not suitable for OS penetration testing, because all those pre-installed security updates are not removable.
Set up Vunlerable Windows XP Virtual Machine
In our own PenTesting teaching, we always use the WinXP VM image file we downloaded many years ago when Microsoft still provided it. Instuctors have to find a way to obtain such WinXP image file by themselves. Assume that you have already obtained the original WinXP VM image. Here is the way to create vulnerable WinXP:
- Import the WinXP image into VirtualBox and run it
- Disable 'automatic update' first
- Go through 'Control Panel' -> 'Add/remove programs' -> click 'Show update'.
- Remove ALL windows security patches manually, one by one! To save time, just ignore all warnings during removal, and be sure to choose 'do not restart now' option if a patch removal requires you to restart windows to be effective. You just need to restart WinXP once all security patches have been removed.
- There are more than 60 security patches, so be patient! It takes aboutn 20 to 25 minutes to finish ALL security patches removal.
After all security patches being removed, you can create the vulnerable WinXP VM image for others and students to use. On VirtualBox, click menu 'File' --> 'Export appliance' to generate a single .ova image file. Since the WinXP VM is valid for 30 days, the created vulnerable WinXP VM would be good to use for PenTesting for 30 days as well.
If you want to conduct this WinXP PenTesting in the future, please use the original WinXP .ova file and repeat the security patch removal process in order to create a fresh vulnerable WinXP for the next 30-day usage.
We wanted to use the PowerShell script developed by us to automatic this patch removal process. Unfortunately, Windows XP does not support PowerShell. Another automatic way we presented in our ASEE'2019 published paper (PDF) is complicated to execute thus does not save much time compared with the above manual patch removal method.
Automatic Security Patch Removal to Create Vulnerable Windows 7 Virtual Machine:
In the Windows 7 VM image provided by Microsoft, the OS has pre-installed around 120 security patches. Thus manual patch removal is not scalable and too time consuming. Fortunately, Windows 7 supports PowerShell script execution, and we have produced a PowerShelll script that can automatically removal partial or all security patches. The script can be downloaded here. The detailed PowerShell code is shown in the following figure:
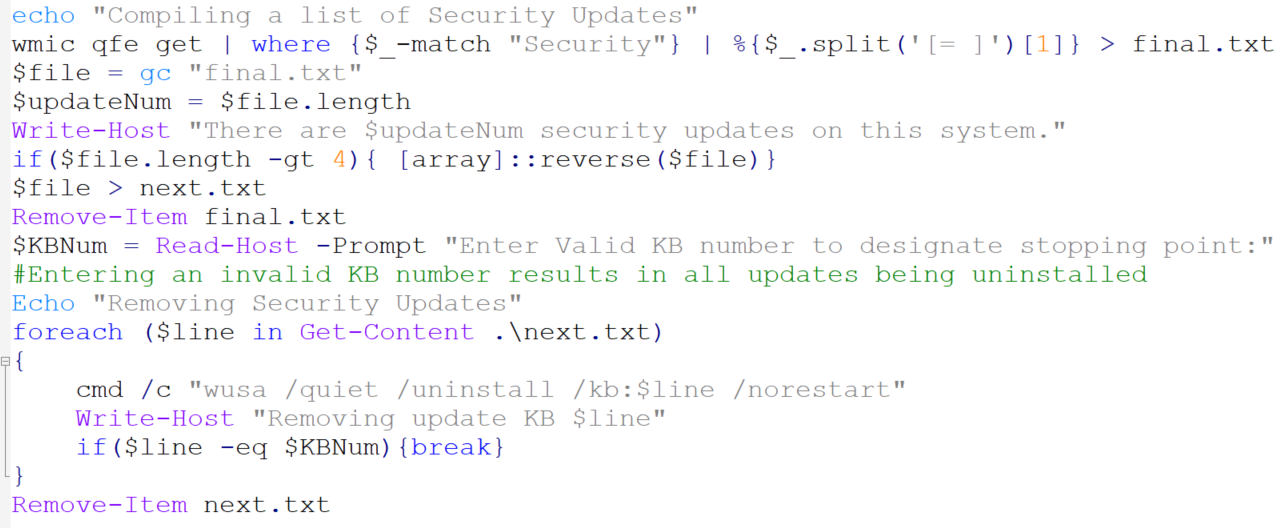
Figure 1: PowerShell script to remove partial or all security patches in Windows 7 Virtual Machine
In Microsoft Windows, all system patches are named starting with 'KB' followed by a unique identification number, which sequentially increases according to the patch release time.
Automatic Removal of All Security Patches:
The following is the procedure to use our PowerShell script to remove all security patches:
- Copy the script into your Windows 7 Virtual Machine. You can use 'Shared folder' option to do it, or you can use Browser to download it after you put it on a website.
- In Win7 start menu search field, search for 'powershell'. Right click the 'Windows Powershell' and click 'Run as Administrator' option. The screenshot is following.
Figure 2: Run PowerShell as adminstrator in Windows 7
- In the PowerShell command window, run 'Set-ExecutionPolicy -ExecutionPolicy Bypass -Scope Process'. This will enable executing a local unsigned PowerShell script in the current session. At the prompt, answer 'Y' to confirm this execution policy change.
- Type the script name and press enter to execute the patch removal script. When the script prompts you to 'Enter Valid KB number to designate stopping point', just type in a random number (will explain this operation's role later). The screenshot is following. It shows that there are 116 security updates in the IE8 Windows 7 virtual machine provided by Microsoft (there are 101 secuirty patches in the IE11 Win7 VM). Please be patient since this patch removal take a while to complete.
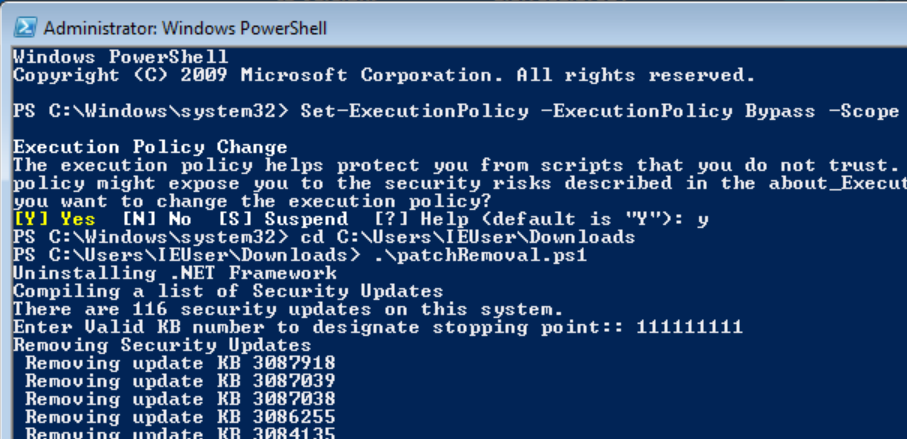
Figure 3: Run the patch removal script in Windows 7 Powershell
Note: We tested on both the IE8 Win7 VM and IE11 Win7 VM provided by Microsoft, and the patch removal script works on both systems. In both systems, the first run of the script will leave 8 security updates remained. If you run the script for the second run, there will be only one OS security update left in both systems, KB2884256, which cannot even be manually uninstalled.
Automatic Removal Security Updates According to Patch Timeline:
In the real world, a Windows computer may have more complicated security status, not being in either the full-patched mode or the completely unpatched mode. Therefore, to better traing students dealing with real world scenarios, we need to create a partially patched and partially vulnerable Windows system.Since Microsoft names its security updates with a sequentially increasing number following patch release timeline, our patch removal script can automatically removing security patches up to a specific key point along the timeline. This is feasible because we can obtain the accurate patch timeline information from Microsoft Security Bulletin. For example, the following figure shows four well-documented security updates of Windows XP that patches critical security vulnerabilities, and thus we can create four different VMs with different sets of vulnerabilities by applying patch removal reversely over security patches whose KB number is larger than each of those four illustrated patch numbers.
Figure 4: A timeline of Windows XP security updates
Security Patch Removal for Windows 8 Virtual Machine:
In Windows 8 virtual machine provided by Microsoft, the patch removal script can be simply executed by right-click the script file and select 'Run with Powershell'. There is no need to change Powershell execution policy.
The current Win8 VM has 12 security updates. After script execution, there are two 'Hotfix for Microsoft Windows' patches left, and you can manually uninstall these two hotfix to make the Windows 8 VM vulnerable.
The following figure shows how to read the 5 register values from Slave 2. Note that the 'data_address' 0 means the address 1 on ModbusPal GUI panel.Security Patch Removal for Windows 10 Virtual Machine:
In Windows 10 virtual machine provided by Microsoft, the patch removal script can be simply executed by right-click the script file and select 'Run with Powershell'. There is no need to change Powershell execution policy.
Disabling automatic update in Windows 10 is not straightforward. You can achieve this by following the instruction here.
However, there are two security updates (KB4470788, KB4509095) in Windows 10 VM that cannot be removed by either our script or manually.